Lock Blog
A resource for consumers, locksmiths, and security professionals
A resource for consumers, locksmiths, and security professionals

Advances in technology have provided us a variety of devices to improve our lives. Biometrics, in particular, is being used in several applications and is defined as identifying unique physical characteristics or traits of the human body. Differences from one human to another serves as that person’s unique identification such as retinal, iris, fingerprint, palm print, and DNA. Biometrics collects and stores this information and recalls it to match a person’s identity.
The combination of biometric data systems and biometrics recognition and identification technologies creates the biometric security systems. The biometric security system is a lock and capture mechanism to control access to specific data. In order to access this system, an individual needs to provide their unique trait that is then matched to a database in the system. If there is a match, the locking system will provide access to the data for the user. The locking and capturing system will activate and record the data of users who accessed the data. The relationship between the biometric and biometric security system is also known as the lock and key system. The biometrics security system is the lock and the biometrics is the key to open that lock.
There are seven basic criteria for a biometric security system:
Uniqueness is the prioritized as the first requirement for biometric data since it is the single factor that can identify the differences of individuals amongst a group of users. Universality is the secondary criteria which indicates requirements for unique characteristics of each person in the world that can not be replicated. Permanence is required for every single trait recorded in the database of the system that needs to be constant for a certain period of time and is most affected by the age of a user. Collectability requires the collection of each trait in order to verify their identification. Performance then outlines how well the security system works. The acceptability parameter will choose fields in which biometric technologies are acceptable. Lastly, circumvention will decide how easily each trait can lead to failure during the verification process.
Physical access control covers identity authentication processes that require users to provide physical characteristics. It is used in high-security locations such as hospitals, police stations, and the military. The most common use for physical access control is applied to doors or computers. This application is entrusted with a high level of security and eliminates the process of identifying complex passcodes. It is a safe and secure method of security.
Logical access control refers to a scheme control over data files or computer programs that contain the private information of multiple users. Logical access control is used by the military and governments who need the highest of security of their information. The only difference between physical and logical access control is that the latter is used for computer networks and system access control and is more secure and effective in protecting and maintaining privacy over the data in the system.
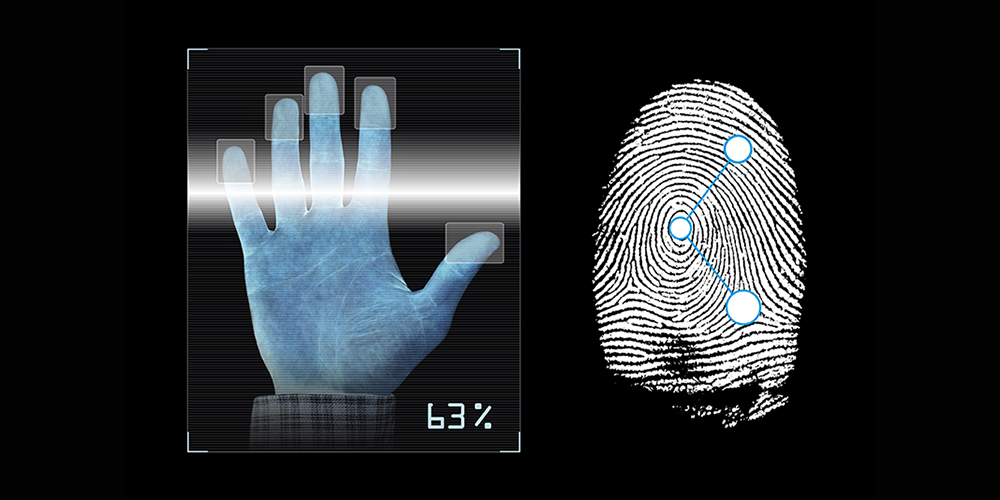
A fingerprint is made of a number of ridges and valleys on the surface of each finger and is unique to each individual. Ridges are the upper skin layer segments of the finger and valleys are the lower segments. The ridges form two minutiae points: ridge endings, where the ridges end, and ridge bifurcations, where the ridges split in two. The uniqueness of a fingerprint can be determined by the different patterns of ridges and furrows as well as the minutiae points. Optical and ultrasound technologies are designed with tools to capture the surface of the fingerprint for verification during the identification of users.
The two algorithms used to recognize fingerprints are minutiae matching and pattern matching. Minutiae matching compares details of the fingerprint by location whereas pattern matching compares all the surfaces of the finger at once. The system is easy to use and install requiring inexpensive equipment with lower power consumption. The main drawback is if a fingerprint is damaged and can not be read. Fingerprint security systems are widely used with applications such as cell phones, laptops, USB flash drives as well as smart locks and other home automation devices. It is also used in judicial systems and for building and home security applications for authorized users to gain access.
Facial recognition detection is used in biometric security systems to identify a user. The human face is one of the easiest characteristics to identify therefore more widely used because it doesn’t require any physical contact between the user and the device. Cameras scan the user’s face and match it to a database for verification. It is easy to install and doesn’t require expensive hardware. Though highly popular, facial recognition technology is still not as unique as its counterparts such as retinal, iris or DNA so it is used with other characteristics in the system.
Biometric face recognition systems will collect data from the user’s face and store it in a database for future use. It is able to measure the overall structure, shape, and proportion of the nose, ears, jaw, eye size, the distance between the eyes, mouth movements like smiling and other expressions such as crying and wrinkles on the face. The most negative factor with this type of technology is that as the user ages their features change.
The iris of they eye is a thin circular structure that is responsible for controlling the diameter and size of the pupils. It controls the amount of light that is allowed through to the retinol to protect the eye’s retina. Iris color varies from person to person depending on the genes of the individual. It has its own unique colors and patterns for each person. Iris recognition analyzes over 200 points of the iris and saves the information in a database for future use to compare it every time a user wants to access the system. Iris recognition security systems are considered the most accurate. The system is expensive and requires installation equipment. It can even recognize characteristics if the user is wearing glasses or contact lenses and even if the user has had eye surgery.
One of the most recent biometric technologies invented is the vein recognition system. It can identify the veins and blood vessels that carry blood to each individual’s heart uniquely. The vein recognition system focuses on veins in the user’s hands. Each finger on a human hand has veins that connect directly to the heart with its own physical traits. The system captures images of the vein patterns inside the user’s fingers by applying light transmission to each finger. It works by passing near-infrared light through the fingers so a camera can record vein patterns. These systems are gaining more attention by experts because of the additional capabilities they have over biometric technologies. They have the greatest level of accuracy and reliability by comparison. The installation and equipment are less expensive and the time it takes to verify each individual is shorter than other methods.
Each person’s DNA is unique which makes it impossible to fake this characteristic. It contains some trait from his or her parents and each cell in the human body contains a copy of this DNA. A DNA Biometric System goes through several steps to collect this information. A sample of DNA is collected primarily through blood, saliva, hair, semen or tissue. It then breaks down the samples into small fragments that contain VNTR (variable number tandem repeat) which repeats at a number of distinctive loci. This makes up the individual’s DNA profile. The size of each DNA fragment is measured and sorted before it is compared to different samples. This method is still considered relatively new and hardly applied in public. It requires expensive equipment and time to collect samples. Due to these limitations, this method is not used as much as other methods.
Two main factors make a voice unique, the physiological component known as the voice tract and a behavioral component known as the voice accent. Combining both of these makes it nearly impossible to imitate another person’s voice exactly which makes the voice a great characteristic for biometric technology. Voice recognition mainly focuses on the vocal tract since it is a unique characteristic of a physiological trait and works well in physical access control for users. This type of system is easy to install and requires minimal equipment that includes microphones, telephones or PC microphones.
Because the performance of users can vary slightly, they are asked to repeat a short passphrase or a sequence of numbers or sentences so the system can analyze the voice most accurately. A downside is that unauthorized users can record another user’s voice and run it through the verification process to gain access control to the system. To prevent this, a voice recognition system will ask users to repeat random phrases provided by the system during the verification phase.
Currently, biometrics technology is considered one of the best security methods of user information and data and is becoming more widely used in consumer applications. It has been used in hospitals, airports, government and law enforcement to keep people safe from a variety of situations. It eliminates the chance of key cards for electronic locks being duplicated or changed and will reduce the chance of identity fraud, a problem that runs rampant throughout our society today. In security applications, it will reduce the amount of criminal activity in homes and business on a large scale. Most agree that overall, it will change our lives for the better.
Category: Lock Types, Safety & Security