Lock Blog
A resource for consumers, locksmiths, and security professionals
A resource for consumers, locksmiths, and security professionals

Master keys are something that many people seem to be fascinated with. The fascination, I believe, is due to the confusing nature of the device. How is one key, opening two doors, but another key that is opening one of those doors is not opening the other? Is it the key that is special? Is it the internal mechanics of the lock? Well, I must warn you that there is some math involved in these answers. Now before you stop reading (I may have lost some people already) it is nothing too difficult. At the lowest level of comprehension it is addition and subtraction, and at the highest level of understanding (at least what is expressed here) it is exponents. It is nothing scary. After reading this piece, you should be able to understand any master key system, varying from the simplest version to the most complex. With the basic understanding, one should be able to extrapolate potential additions to the system’s security.
In order of least access to most access:
Change Key – This key is also referred to as a sub-master key. It will open one lock and only locks that are exactly the same. The lock that the change key opens will also open with the use of the master key, and any key above that rank.
Master Key – Without a master key, there is only one key for a lock. This is the necessary key to change a simple lock into a master keyed lock. In some systems, this will be the highest ranking key. In the trade, a master key may be shortened to ‘MK’.
Grand Master Key – A grand master key is used to access multiple master key systems. This key will open every master system under it, and the subsequent change keys under those systems. In the trade, a master key may be shortened to ‘GMK’.
Great Grand Master Key – The great grand master key will open all the grand master key systems under it, the master key systems under those, and the change keys under those. Theoretically, this trend can continue until the locks become too complicated to function. There could be grand master keys prefaced with great great great great, etc. etc.
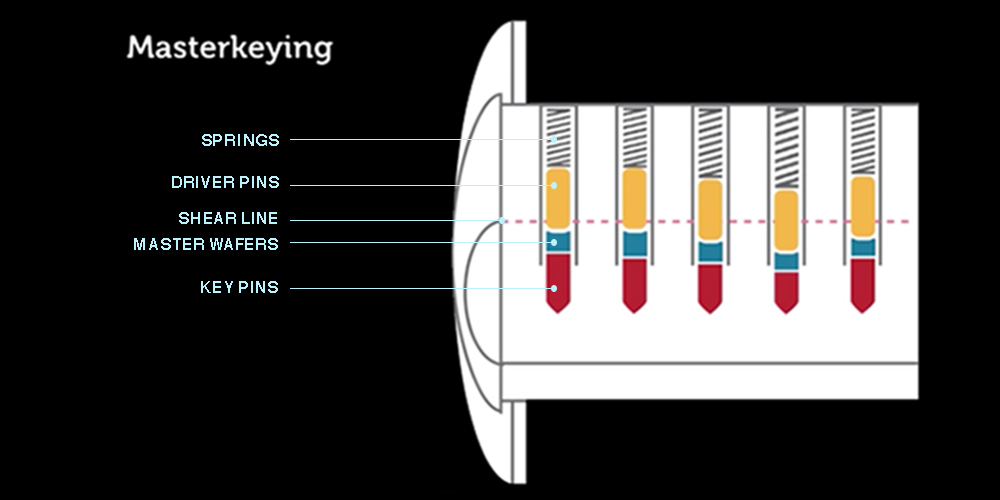
Most master key systems work off of a basic pin tumbler lock. A quick review on how a basic pin tumbler lock will work: To open a lock a pin stack consisting of a driver pin and a key pin must be elevated so that the two rest on opposite sides of the shear line. A key lifts key pins within a lock. These key pins are all different sizes. The driver pins will be a universal size. Therefore, the key needs to have the right set of grooves to lift the key pins to the correct height. It is an oversimplification, but if you would like to find out more about the specifics you can check out the house lockouts section of our website. With that understanding, it will be easier to comprehend the addition of a master key system. All that is needed for any standard pin tumbler to be converted for a master key system is to add a master wafer (aka master pin) between a driver and key pin. A master wafer is virtually a small hockey puck shaped pin. Once it is in place, the pin stack will have two shear lines. A shear line for a pin stack with a master wafer below or above the line.
Most large institutions do not want their employees to carry around large quantities of keys. Similarly, these institutions would like to restrict access based on an individual’s standing, and responsibility, within the establishment. A master key system will allow for different levels of restricted entry. When a master key system is finished there may be a graduated level of access. In the example of a property manager, one tenant’s key will work on their lock but not on the neighbor’s lock. However, the property manager will have one key that works for both locks. This can work to create a number of possible keys. Say there are five chambers in the lock and five active pin stacks. If each one of those stacks has a master wafer, then each chamber will have two possible shear lines. That is 2 x 2 x 2 x 2 x 2, or two to the fifth power (2^5), which equals a total of 32 possible unique keys. Of those 32 possible keys, only two keys need to be made. One will be for the person with access to what that lock is securing, and another for the person that has access to what every lock is securing in the location.
It is often the case that convenience will lower security. The more convenient something is for the proper user, the simpler it is to defeat (like some of these locks for instance). Master keyed locks are a great example of this. A master key system will make your locks vulnerable to several types of attacks:
Exploratory keys are used to decode master keyed systems with only your change key and the lock it opens. To do this, the first key in the cycle of exploration will have a zero cut (no cut, as if this groove was blank) on what would be the groove closest to the key’s shoulder. With the knowledge of what type of key it is, you can gather the key codes, and cut the zero cut to a one. Try out that key. Once you have worked your way down to the deepest groove depth, you should have an understanding of the pinning on that first cut in the key. If there is only one depth that turns the lock, then there is no master wafer. If the lock opens at two depths, then it does have a master wafer in the first pin stack. There may be more shear lines if there are more wafers or pins. With the next exploratory key, keep the depth closest to the shoulder at the only functioning depth or at the depth that the original key did not have. Have the next cut at zero, and then begin the process again.
This process will be repeated with each groove in the bitting. Each time you make another exploratory key, you will keep the only working depth or the depth that your original key did not have. To save time in the exploration process, you can assume that there are no master wafers that are changing the depth value by a factor of one either higher or lower than the depth on your working key. Master wafers with a differential of one depth are often not used because they can jam up the internals of a lock. The lock you are working on may have one depth wafers, but assuming it won’t, will potentially save you time. Once you have a key that works in your own lock, that has as many different cuts as possible, you will know all the possible keys that will work in your lock. You will have to fashion a key for each possibility.
To find a number of keys you will need, use the formula two to the power of ‘n’ (n= the number of chambers with a master wafer) i.e: A lock that has master wafers in 3 chambers would have 8 possible keys. The ‘two’ can vary if there are multiple master wafers in a chamber. Multiple master wafers will be used to make more complicated systems, such as grand Master Keys, and Great Grand Master Keys. If the system is on a Grand Master, Great Grand Master, or anything higher, the number of functioning key codes you end up with will increase accordingly. For every additional master wafer, you must add one extra shear line to the chamber.
Another way you can cut down time in your decoding is to do some research on the lock. If the lock is a Kwikset, then it will have a Maximum Adjacent Cut Specification (MACS) of four. That means that a cut on either side must not exceed a difference of four. For example, a key can have the bitting 2, 4, 5, 2, 6. The difference between 2 and 4 is 2; the difference between 4 and 5 is 1; the difference between 5 and 2 is 3; the difference between 2 and 6 is 4. If the 4th groove had been a one, then the difference would have been 5 between grove 4 and 5. That would have violated MACS. Because this will never happen, when you are decoding for this key you would know that there is no possible key with the bitting 2, 4, 5, 1, 6. So out of your possible 32 biting combinations that you may need to try, there are perhaps some that can be crossed off the list before you make them.
Adding master wafers to your lock will hurt your security, with a few exceptions. However, as long as a master wafer creates a secondary and functional shear line, security will be compromised. Essentially, there are two different ways to pick each chamber. In a five chamber lock, with a master wafer in each, there are 32 different ways to pick the lock. This increase in picking weakness will make the lock more susceptible to raking as a bypass method. Due to the fact that any amateur can rake a lock, the number of individuals that can open your locks dramatically increases. In the security industry, the amount of skill it takes to defeat your protections is directly correlated to the amount of crime being deterred. Even though your system’s vulnerability to picking may be increased dramatically it is up to you to assess your risk. Are picking attacks common in your area, industry, etc? You will also need to weigh how much having a master key system will help your security in terms of key control and personal convenience.
As we discussed early on, a master key system will make one lock open with the use of at least two keys. If you are looking to make a master key or master key system, the first step will be to gather two keys with the same style. Once you have these keys, you will need to decode their depths. You can do this most easily with a key gauge. In the event that you do not have a key gauge, you will need to get creative with the tools you do have. If you are a locksmith or have the tools and time to make a key with the exact cuts you want, there is no need to use two existing keys. You can also purchase a pinning kit if you wish to do this work more often. Regardless of whether you will be making keys or using pre-existing ones, note the existing, or intended, groove depths. For our theoretical example we will say that these are our keys:
Key #1 = 2, 4, 5, 2, 6
Key #2 = 4, 2, 5, 4, 6
Next, gather a lock that the key type will fit in, for our example these keys will be Kwikset. You should have the ability to rekey the lock, so you can access the pins. Now we begin creating the master key system.
1) Compare groove depths vertically (2 and 4; 4 and 2; 5 and 5; 2 and 4; 6 and 6) and mark the shallowest one in a set:
Key #1 = 2, 4, 5, 2, 6
Key #2 = 4, 2, 5, 4, 6
2) Write down all of the shallowest depths in the correct order. In our case, this would be 2, 2, 5, 2, 6. (If a depth repeats that is the lowest depth.)
3) Subtract the lowest number from the vertically adjacent number.
ex: 4 – 2 = 2; 4 – 2 = 2; 5 – 5 = 0; 4 – 2 = 2; 6 – 6 = 0
4) Write down the numbers in the correct order. ex: 2, 2, 0, 2, 0
5) The number list from step 2 will be the bottom pins, and the number list from step 4 will be the values for the master wafers. ex:
Master Wafers: 2, 2, no master wafer, 2, no master wafer
Bottom Pins: 2, 2, 5, 2, 6.
6) Gather the correct pins and wafers. ex:
Master Wafers: 0.045, 0.045, no master wafer, 0.045, no master wafer
Bottom Pins: 0.195, 0.195, 0.265, 0.195, 0.285
7) Open the lock, and remove the existing pins. (You may keep the pins for any chamber that is not having a master wafer added. In our example that would be chambers 3 and 5.)
8) Place pins in their proper chambers beginning with the bottom pins, then add the corresponding wafer.
9) Reassemble the lock.
10) Try out both keys.
Once you have a working lock, that can be opened with two keys, one of the keys can be assigned as the master and the other as the change key. To continue building out the master key system, simply repeat this process with your master key, a third key, and a second lock. Try to stay away from using number one master wafers. If you are just using keys that you have, there may be no way around it, but in a professional setting only master wafers with a value of two or greater should be used. As I have previously stated, the smaller the master wafer is the higher the risk of damaging the lock, which will result in having to call a locksmith to repair damaged locks.

There are additional security measures, meant to keep your home safe, that can be added onto a master-keyed system. These auxiliary precautions will make picking and decoding more difficult, but not impossible. Adding sidebars and active elements to the key will make exploration much more complicated. A master system does not even need to use a pin tumbler type lock. Disk detainer locks can be mastered to serve as a more complicated and secure means of protection.
As the protections are added, the lock will need to become more complex. Whenever you are adding security be careful that you are comprehending the complexity of the system. My general rule is, “If you cannot take it apart and put it back together, you should not be making your own”. If you are brainstorming your very own ideas about additional security, I would recommend researching your idea. In the rare case that someone has not already had your idea, try and find a device that works similarly or in a more basic way than your idea. This is the mechanism that should be deconstructed and understood. Test all additional security before using it in your operational security.
A master key system allows two or more keys to open one lock. To make a master key system, you need locks and keys that are the same make and model, and a way to rekey those locks. The basic pin tumbler master locks use a master wafer/pin in between the key pin and the driver pin. Although these systems often use pin tumbler locks, they can use different lock types for varying levels of security. The main selling point for master keys is that they limit the amount of keys needed to open multiple locks. These systems can get pretty complicated with the introduction of grand master keys and great grand master keys.
The more master wafers, the more keys there are that can open the lock because the number of shear lines increases. Master key systems are very susceptible to picking and decoding. The easier a lock is to pick, the more thieves there are who can steal from you. Completing a risk assessment will give you a deeper understanding of whether or not your threats and vulnerabilities should concern you. Anytime you are attempting any work on your own security, evaluate your strengths and weakness. There is no need to break your door locks (an important part of home security) in the hopes of saving a few dollars. Do not use any of this information for criminal activity. This post is intended for educational purposes only. Be safe, and know your security.
Category: Commercial, How To's